CTB-Locker Ransomware Infects Thousands of Web Servers
In last few years, we saw an innumerable rise in ransomware threats ranging from Cryptowall to Locky ransomware discovered last week.
Now, another genre of ransomware had been branched out from the family of CTB-Locker Ransomware with an update to infect "Websites", according to Lawrence Abrams of BleepingComputer.
The newly transformed ransomware dubbed "CTB-Locker for Websites" exclusively hijacks the websites by locking out its data, which would only be decrypted after making a payment of 0.4 BTC.
This seems to be the very first time when any ransomware has actually defaced a website in an attempt to convince its administrator to comply with the ransom demand.
However, the infected website admins can unlock any 2 files by the random generator for free as a proof of decryption key works.
Here's How CTB-Locker for Websites Ransomware Works
Lawrence explained that CTB-Locker ransomware replaces the index page (the original index.php or index.html) of the servers hosting websites with the attacker's defacement page (a new affected index.php).
The defacement page serves a message informing the site owners that their files have been encrypted, and they need to pay a ransom before a certain deadline.
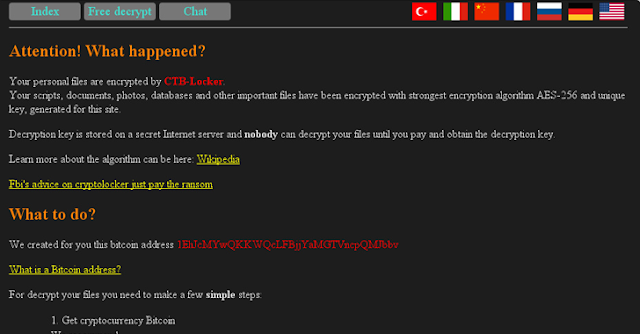
Once encrypted, the compromised websites display the following message:
"Your scripts, documents, photos, databases and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this site."
The message also contains a step-by-step guide that helps the CTB-Locker victims to make the payment to a specific Bitcoin address.
FREE Key to Decrypt Any 2 Random Files
Soon after gaining the website control, the ransomware attacker submits two different AES-256 decryption keys to the affected index.php.
The first key would be used to decrypt any 2 random files from the locked files for free under the name of "test" which are chosen to demonstrate the decryption procedure.
Once the site administrator enters the filename and hit "Decrypt for Free," jquery would be fired up upon the request to test the decryption key in a C&C Server. When the key is received, it'll decrypt any 2 random files and display 'Congratulations! TEST FILES WAS DECRYPTED!!'
The other decryption key would be the one to decrypt rest of the seized files, after making the payment in Bitcoin to the attacker.
All the website's content would be encrypted using an AES-256 algorithm, and a unique ID would be generated for each infected website.
Nearly all possible types of files extensions are being affected by CTB-Locker Ransomware.
Live Session with Ransomware Attackers
Another unique characteristic of the ransomware is giving victims the ability to exchange messages with the ransomware attackers, noted by Lawrence in his blogpost.
The ransomware developers have organized a chat room in such a way that the victims could talk with the ransomware creators after the specifying name of the secret file which is present in the same directory with index.php.
CTB Locker for Website → Modifies Packages in the Server
The CTB-Locker for Website package utilizes a variety of files described below:
- index.php : The Main component of CTB-Locker for Websites and contains the encryption and decryption routines as well as the payment page.
- allenc.txt : Contains a list of all encrypted files.
- test.txt : Contains the path and filenames to two prechosen files that can be decrypted for free.
- victims.txt : It contains a list of all files that are to be encrypted. However, the files that are already encrypted will remain in this list.
- extensions.txt - The list of file extensions that should be encrypted.
- secret_[site_specific_string] : The secret file used by the Free Decrypt and Chat functions and is located in the same folder as the index.php file.
Command and Control Server Location:
According to Benkow Wokned (@benkow_), a security researcher who discovered CTB-Locker for Website, found that the index.php page utilizes the jQuery.post() function to communicate and POST data to the Ransomware's Command and Control (C&C) servers.
Currently, there are three Command and Control servers for CTB-Locker for Websites uncovered by the researchers:
- http://erdeni.ru/access.php
- http://studiogreystar.com/access.php
- http://a1hose.com/access.php
The ransomware also gives a timeslot for the website administrators to recover the files. However, failure to pay the BTC in time would double the ransom amount by 0.8 BTC.
CTB-Locker for Windows
CTB-Locker for Websites isn't the only latest development with this family of ransomware. The ransomware has come to the Windows environment by using executables code signed with a stolen certificate.
Usually, the purpose of digital signature is to authenticate the public about the genuinity of the products. The certificates are provided only after a background check conducted by the Certificate Authorities (CA) like Verizon, DigiCert.
But the cybercriminal group behind the CTB-Locker ransomware has tampered the genuinity of digital certificates. The executable version in the Windows of the CTB Ransomware comes with a pre-signed digital signature.
Uses Encryptor Raas For Code-Signing Certificate
The group behind CBT believed to had taken the advantage of Jeiphoos, another ransomware developer who lets people go to his "Encryptor RaaS" Tor site that provides free digital signature certificates and sign any executable using stolen code-signing certificate.
The act of stealing digital signatures is not new as they are included in the frames from the past years.
Hijacking a company website would economically affect the services that are being offered to users via websites, elevating the issue to another level. However, the major part lies in the POS (Point of Sale) attack, if the threat infects an e-commercial website.
Currently, many websites had been compromised by "CBT-Locker for Website." As per the analysis, many wordpress sites (most of the static web pages) has been found to be targeted by CBT Website Locker.
Since this is not a serious issue like the Locky ransomware that utilizes Macros, the website administrator can make use of the untouched mirrors (backups) to bring back the site into action.


Comments
Post a Comment