Emotet Evades Antivirus Detection With Camouflaged Malicious Macros
A new Emotet Trojan variant has been observed in the wild with the added ability to hide from anti-malware software by embedding malicious macros used to drop the main payload inside XML files disguised as Word documents.
Emotet (also known as Geodo or Heodo) is a modular Trojan developed by the Mealybug threat group and used by attackers to infect targets via spam e-mails, leading to the theft of financial information such as bank logins or cryptocurrency wallets.
The Trojan is also designed to act as a carrier conduit for other banking Trojans or for information-stealing and highly-customizable modular bots such as Trickbot.
Hides in plain sight
Menlo Security detected a new variant of the Emotet Trojan active since mid-January, which obfuscates the initial infection VBA macro code to minimize anti-malware detection levels.
The Menlo Security research team observed two variants of the malware distributed by the mid-January campaign. The first which accounted for 80% of all samples, delivered malicious XML files camouflaged as DOC documents.
The first type, and the more prominent one, was an XML file that contains the standard XML header, plus the Microsoft Word Document XML format tags. This is followed by Base64 encoded data, which contains the compressed and obfuscated VBA macro code. The file itself was named with a .doc extension.
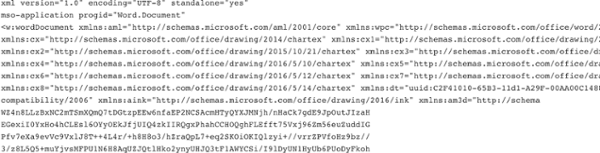
The second type of malicious documents, which made up 20% of the rest of all detected samples, were standard Word files which also contained malicious macro code.
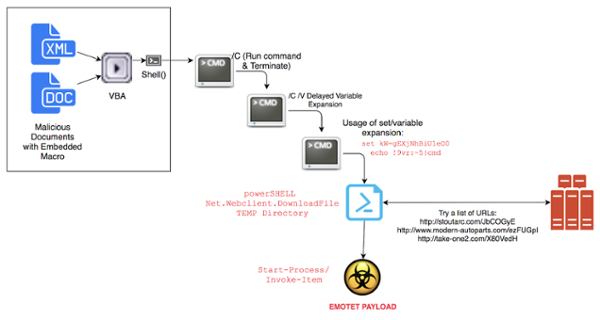
The infection procedure is quite complex and it follows a sequential structure, with the initial malicious script spawning multiple processes which will launch a Powershell script that downloads the Emotet payload to the TEMP folder on the compromised machine.
Once Emotet Trojan arrives on the infected host, it will be launched and starts connecting to "a list of URLs (probably the attacker’s command-and-control servers) in a loop and breaks when one succeeds."
This new detection evasion capability added to Emotet by MealyBug is in line with previously observed behavior. As US-CERT says in its TA18-201A advisory:
Emotet is a polymorphic banking Trojan that can evade typical signature-based detection. It has several methods for maintaining persistence, including auto-start registry keys and services. It uses modular Dynamic Link Libraries (DLLs) to continuously evolve and update its capabilities. Furthermore, Emotet is Virtual Machine-aware and can generate false indicators if run in a virtual environment.
Additionally, Emotet is known to be very active, showing up in new malware campaigns almost every month, from October when it was updated to steal its victims' emails going back six months and November when it moved its Command & Control infrastructure to the US.
Also, the Trojan was revived in another November campaign which delivered the malware through emails designed to look as coming from financial institutions or disguised as Thanksgiving-themed greetings for employees.
Back in January Emotet came back again in the form of an updated variant capable of checking if the recipient's/victim's IP address is either blacklisted or on spam lists maintained by Spamhaus, SpamCop, or SORBS.
Menlo Security also provides a full list of indicators of compromise (IOCs) such as payload hashes, domains used by the malware campaign and IP addresses of C&C servers, as well as PowerShell callback URLs at the end of their analysis.
Source:Bleepingcomputer.com



Comments
Post a Comment